Attempting to wade my way through getting a simple P2P setup in place while utilizing the encryption features in RUI3. Here is my setup.
3x RAK3172 modules. Two of them acting as senders and the third acting as a receiver.
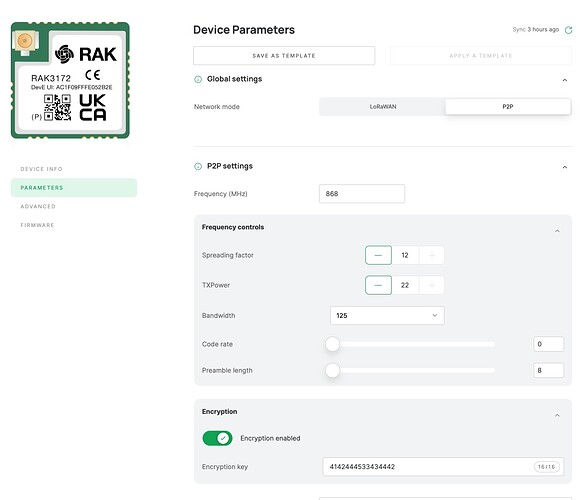
The two senders are running firmware version 3.4.2 and are configured via WisToolBox with the following parameters - all default aside from the encryption key and mode being set to P2P.
The receiver module is programmed with the LoraP2P example Arduino sketch. The only thing I have altered here is the addition of the encry.set() and enckey.set() functions as the docs outlined LoRaWAN | RAKwireless Documentation Center
Serial.printf(“Set P2P mode encryption status %s\r\n”, api.lorawan.encry.set(1) ? “Success” : “Fail”);
Serial.printf(“Set P2P mode encryption Key %s\r\n\r\n”, api.lorawan.enckey.set(node_encrypt_key, 8) ? “Success” : “Fail”);
Serial.printf(“P2P encryption status = %s\r\n”, api.lorawan.encry.get() ? “Enable” : “Disable”);
api.lorawan.enckey.get(encrypt_buff, 8);
Serial.printf(“P2P encryption Key = 0x”);
for (int I = 0 ; I < 8 ; I++) {
Serial.printf(“%02X”, encrypt_buff[I]);
}
Serial.println(“”);
The result is that with the encryption turned off on the sending modules, the receiving module prints out the payload as expected. But when the sending modules have the encryption option enabled, the receiving module does not seem to decrypt the payload.
RAKwireless LoRaWan P2P Example
------------------------------------------------------
P2P Start
Hardware ID: stm32wle5xx
Model ID: rak3172
RUI API Version: 3.2.0
Firmware Version: 3.4.2-rui3_22q1_update.112
AT Command Version: 1.5.4
Set Node device work mode Success
Set P2P mode frequency 868.000: Success
Set P2P mode spreading factor 12: Success
Set P2P mode bandwidth 125: Success
Set P2P mode code rate 4/5: Success
Set P2P mode preamble length 8: Success
Set P2P mode tx power 22: Success
Set P2P mode encryption status Success
Set P2P mode encryption Key Success
P2P encryption status = Enable
P2P encryption Key = 0x4142444533434442
P2P set Rx mode Success
Current Work Mode: LoRa P2P.
+EVT:RXP2P RECEIVE TIMEOUT
Empty buffer.
P2P send Success
P2P set Rx mode Success
+EVT:RXP2P:-21:12:FFA4ABD50A627F9A09BAD44F2287AB06
Incoming message, length: 16, RSSI: -21, SNR: 12
+------------------------------------------------+ +----------------+
|.0 .1 .2 .3 .4 .5 .6 .7 .8 .9 .a .b .c .d .e .f | | ASCII |
+------------------------------------------------+ +----------------+
0.|48 65 6c 6c 6f 20 57 6f 72 6c 64 00 00 00 00 00 | |Hello World.....|
+------------------------------------------------+ +----------------+
P2P send Fail
+EVT:RXP2P:-22:22:48656C6C6F20576F726C64
Incoming message, length: 11, RSSI: -22, SNR: 22
+------------------------------------------------+ +----------------+
|.0 .1 .2 .3 .4 .5 .6 .7 .8 .9 .a .b .c .d .e .f | | ASCII |
+------------------------------------------------+ +----------------+
0.|6e d3 68 da 71 bb c1 70 46 d8 a1 | |n.h.q..pF.. |
+------------------------------------------------+ +----------------+
P2P send Fail
I am unsure if there are other steps needed to decrypt the payload on the receiving end, or if setting the encryption options as shown above should result in that happening automatically.
Anyone else know the details for how to achieve this? Appreciate it!