Hi all,
Device: RAK7258 LTE, firmware version LoRaGateway_1.1.0053_Release_r187
Can I ask how to properly set up OpenVPN in RAK7258? I can not find instructions for this.
Reproduce:
-
copy cert, key, ca and tls_auth file to /lib/uci/upload/
-
config /etc/config/openvpn to following
‘’’
config openvpn ‘sample_client’
option client ‘1’
option dev ‘tun’
option resolv_retry ‘infinite’
option persist_key ‘1’
option user ‘nobody’
option verb ‘3’
option remote ‘OPENVPN_SERVER_DOMAIN’
option proto ‘tcp-client’
option key_direction ‘1’
option setenv ‘opt block-outside-dns’
option sndbuf ‘0’
option rcvbuf ‘0’
option auth ‘SHA512’
option cipher ‘AES-256-CBC’
option remote_cert_tls ‘server’
option key ‘/lib/uci/upload/openvpn_key.txt’
option cert ‘/lib/uci/upload/openvpn_cert.txt’
option ca ‘/lib/uci/upload/openvpn_ca.txt’
option tls_auth ‘/lib/uci/upload/openvpn_tls_auth.txt 1’
option enabled ‘1’
‘’’ -
reboot and you will see the system log as below
‘’’
Wed Oct 16 11:13:38 2019 daemon.notice netifd: Interface ‘wwan’ has link connectivity
Wed Oct 16 11:13:38 2019 daemon.notice netifd: Interface ‘wwan’ is setting up now
Wed Oct 16 11:13:38 2019 daemon.notice netifd: Bridge ‘br-lan’ link is up
Wed Oct 16 11:13:38 2019 daemon.notice netifd: Interface ‘lan’ has link connectivity
Wed Oct 16 11:13:38 2019 daemon.notice netifd: VLAN ‘eth0.1’ link is up
Wed Oct 16 11:13:38 2019 daemon.notice netifd: Network device ‘lo’ link is up
Wed Oct 16 11:13:38 2019 daemon.notice netifd: Interface ‘loopback’ has link connectivity
Wed Oct 16 11:13:38 2019 daemon.notice netifd: VLAN ‘eth0.2’ link is up
Wed Oct 16 11:13:38 2019 daemon.notice netifd: Interface ‘wan’ has link connectivity
Wed Oct 16 11:13:38 2019 daemon.notice netifd: Interface ‘wan’ is setting up now
Wed Oct 16 11:13:39 2019 user.notice ping-watchdog: lan br-lan ifup
Wed Oct 16 11:13:39 2019 daemon.notice netifd: wwan (1480): Command failed: Permission denied
Wed Oct 16 11:13:39 2019 daemon.notice netifd: wan (1526): udhcpc: option -h NAME is deprecated, use -x hostname:NAME
Wed Oct 16 11:13:39 2019 daemon.notice netifd: wan (1526): udhcpc (v1.23.2) started
Wed Oct 16 11:13:39 2019 authpriv.info dropbear[1520]: Not backgrounding
Wed Oct 16 11:13:39 2019 kern.warn kernel: [ 45.390000] efuse_probe: efuse = 10000002
Wed Oct 16 11:13:40 2019 daemon.notice netifd: Interface ‘wwan’ is now down
Wed Oct 16 11:13:40 2019 user.notice firewall: Reloading firewall due to ifup of lan (br-lan)
Wed Oct 16 11:13:40 2019 kern.warn kernel: [ 45.570000] tssi_0_target_pwr_g_band = 27
Wed Oct 16 11:13:40 2019 kern.warn kernel: [ 45.580000] tssi_1_target_pwr_g_band = 27
Wed Oct 16 11:13:40 2019 daemon.err uhttpd[1581]: socket(): Address family not supported by protocol
Wed Oct 16 11:13:40 2019 daemon.err uhttpd[1581]: socket(): Address family not supported by protocol
Wed Oct 16 11:13:40 2019 kern.info kernel: [ 45.940000] br-lan: port 1(eth0.1) entered forwarding state
Wed Oct 16 11:13:44 2019 daemon.info loraSrv[1654]: Initializing signal handlers
Wed Oct 16 11:13:45 2019 daemon.warn openvpn(sample_client)[1666]: Unrecognized option or missing parameter(s) in openvpn-sample_client.conf:14: block-outside-dns (2.3.6)
Wed Oct 16 11:13:45 2019 daemon.notice openvpn(sample_client)[1666]: OpenVPN 2.3.6 mipsel-openwrt-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH] [IPv6] built on Oct 15 2019
Wed Oct 16 11:13:45 2019 daemon.notice openvpn(sample_client)[1666]: library versions: OpenSSL 1.0.2j 26 Sep 2016, LZO 2.08
Wed Oct 16 11:13:45 2019 daemon.warn openvpn(sample_client)[1666]: WARNING: you are using user/group/chroot/setcon without persist-tun – this may cause restarts to fail
Wed Oct 16 11:13:45 2019 daemon.warn openvpn(sample_client)[1666]: WARNING: file ‘/lib/uci/upload/openvpn_key.txt’ is group or others accessible
Wed Oct 16 11:13:45 2019 daemon.warn openvpn(sample_client)[1666]: WARNING: file ‘/lib/uci/upload/openvpn_tls_auth.txt’ is group or others accessible
Wed Oct 16 11:13:45 2019 daemon.notice openvpn(sample_client)[1666]: Control Channel Authentication: using ‘/lib/uci/upload/openvpn_tls_auth.txt’ as a OpenVPN static key file
Wed Oct 16 11:13:45 2019 daemon.notice openvpn(sample_client)[1666]: Outgoing Control Channel Authentication: Using 512 bit message hash ‘SHA512’ for HMAC authentication
Wed Oct 16 11:13:45 2019 daemon.notice openvpn(sample_client)[1666]: Incoming Control Channel Authentication: Using 512 bit message hash ‘SHA512’ for HMAC authentication
Wed Oct 16 11:13:45 2019 daemon.notice openvpn(sample_client)[1666]: Socket Buffers: R=[87380->87380] S=[16384->16384]
Wed Oct 16 11:13:45 2019 daemon.err openvpn(sample_client)[1666]: RESOLVE: Cannot resolve host address: OPENVPN_SERVER_DOMAIN: Name or service not known
Wed Oct 16 11:13:45 2019 daemon.notice openvpn(sample_client)[1666]: NOTE: UID/GID downgrade will be delayed because of --client, --pull, or --up-delay
Wed Oct 16 11:13:45 2019 daemon.err openvpn(sample_client)[1666]: RESOLVE: Cannot resolve host address: OPENVPN_SERVER_DOMAIN: Name or service not known
Wed Oct 16 11:13:45 2019 user.emerg syslog: sh: on: unknown operand
Wed Oct 16 11:13:45 2019 kern.info kernel: [ 51.400000] S95done (1668): drop_caches: 1
Wed Oct 16 11:13:47 2019 daemon.info evloop[1657]: evloopInit Done.
Wed Oct 16 11:13:47 2019 daemon.info md[1657]: mdInit Done.
Wed Oct 16 11:13:47 2019 daemon.info mqttEv[1657]: mqttEvInit Done.
Wed Oct 16 11:13:49 2019 daemon.info unknown[1657]: gwManagerInit: Init gateway Manager
Wed Oct 16 11:13:49 2019 daemon.info bufrd[1657]: bufrdInit Done.
Wed Oct 16 11:13:49 2019 daemon.info bufrd[1657]: ENTER bufrdCreate `gwbridge-rd’
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: MQTT Init Start
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: Mqtt - Client ID gwbridge-60c5a8fffe76121b
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: Mqtt - Retain 0
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: Mqtt - Clean Session 1
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: Mqtt - Qos 1
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: Mqtt - keepalive 10
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: CA CERT File null
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: CA PATH /etc/ssl/certs/
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: Client CERT File null
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: Client Key File null
Wed Oct 16 11:13:49 2019 daemon.info gwBridge[1657]: TLS Version : tlsv1.2
Wed Oct 16 11:13:49 2019 daemon.info procd: - init complete -
Wed Oct 16 11:13:50 2019 kern.warn kernel: [ 55.870000] <==== rt28xx_init, Status=0
Wed Oct 16 11:13:50 2019 daemon.notice netifd: Interface ‘wwan’ is disabled
Wed Oct 16 11:13:50 2019 daemon.notice netifd: Interface ‘wwan’ is enabled
Wed Oct 16 11:13:50 2019 daemon.notice netifd: Interface ‘wwan’ is setting up now
Wed Oct 16 11:13:50 2019 daemon.notice netifd: wan (1526): Sending discover…
Wed Oct 16 11:13:50 2019 daemon.notice netifd: wan (1526): Sending discover…
Wed Oct 16 11:13:50 2019 daemon.notice netifd: wan (1526): Sending discover…
Wed Oct 16 11:13:50 2019 daemon.err openvpn(sample_client)[1666]: RESOLVE: Cannot resolve host address: OPENVPN_SERVER_DOMAIN: Name or service not known
Wed Oct 16 11:13:50 2019 daemon.err mqttEv[1657]: mqttEvConnectStart: [[gwBridgeS Mqtt Client]] Unable to connect
Wed Oct 16 11:13:50 2019 daemon.info gwBridge[1657]: MQTT Init Done
Wed Oct 16 11:13:50 2019 daemon.info evloop[1657]: ENTER evloopRun
Wed Oct 16 11:13:51 2019 daemon.notice netifd: radio0 (1474): Interface doesn’t accept private ioctl…
Wed Oct 16 11:13:51 2019 daemon.notice netifd: radio0 (1474): set (8BE2): Invalid argument
Wed Oct 16 11:13:51 2019 daemon.notice netifd: wwan (1751): udhcpc: option -h NAME is deprecated, use -x hostname:NAME
Wed Oct 16 11:13:51 2019 daemon.notice netifd: wwan (1751): udhcpc (v1.23.2) started
Wed Oct 16 11:13:51 2019 daemon.notice netifd: Network device ‘ra0’ link is up
Wed Oct 16 11:13:51 2019 kern.info kernel: [ 57.090000] device ra0 entered promiscuous mode
Wed Oct 16 11:13:51 2019 kern.info kernel: [ 57.100000] br-lan: port 2(ra0) entered forwarding state
Wed Oct 16 11:13:51 2019 kern.info kernel: [ 57.110000] br-lan: port 2(ra0) entered forwarding state
Wed Oct 16 11:13:51 2019 daemon.notice netifd: wwan (1751): Sending discover…
Wed Oct 16 11:13:51 2019 daemon.notice netifd: wwan (1751): Sending select for 10.247.19.203…
Wed Oct 16 11:13:51 2019 daemon.notice netifd: wwan (1751): Lease of 10.247.19.203 obtained, lease time 7200
Wed Oct 16 11:13:51 2019 daemon.notice netifd: Interface ‘wwan’ is now up
Wed Oct 16 11:13:53 2019 kern.info kernel: [ 59.110000] br-lan: port 2(ra0) entered forwarding state
Wed Oct 16 11:13:54 2019 daemon.info mqttEv[1657]: mqttEvRegister : Register mosquitto event [gwBridgeS Mqtt Client]
Wed Oct 16 11:13:54 2019 daemon.info dnsmasq[1779]: started, version 2.73 cachesize 150
Wed Oct 16 11:13:54 2019 daemon.info dnsmasq[1779]: compile time options: no-IPv6 GNU-getopt no-DBus no-i18n no-IDN DHCP no-DHCPv6 no-Lua TFTP no-conntrack no-ipset no-auth no-DNSSEC loop-detect inotify
Wed Oct 16 11:13:54 2019 daemon.info dnsmasq[1779]: DNS service limited to local subnets
Wed Oct 16 11:13:54 2019 daemon.info dnsmasq-dhcp[1779]: DHCP, IP range 192.168.230.100 – 192.168.230.249, lease time 12h
Wed Oct 16 11:13:54 2019 daemon.info dnsmasq[1779]: using local addresses only for domain lan
Wed Oct 16 11:13:54 2019 daemon.info dnsmasq[1779]: reading /tmp/resolv.conf.auto
Wed Oct 16 11:13:55 2019 daemon.info dnsmasq[1779]: using local addresses only for domain lan
Wed Oct 16 11:13:55 2019 daemon.info dnsmasq[1779]: using nameserver 10.4.27.70#53
Wed Oct 16 11:13:55 2019 daemon.info dnsmasq[1779]: using nameserver 10.5.133.45#53
Wed Oct 16 11:13:55 2019 daemon.info dnsmasq[1779]: read /etc/hosts - 1 addresses
Wed Oct 16 11:13:55 2019 daemon.info dnsmasq[1779]: read /tmp/hosts/dhcp - 1 addresses
Wed Oct 16 11:13:55 2019 daemon.info dnsmasq-dhcp[1779]: read /etc/ethers - 0 addresses
Wed Oct 16 11:13:55 2019 user.notice ping-watchdog: loopback lo ifup
Wed Oct 16 11:13:55 2019 daemon.info gwBridge[1657]: mosqConnectCB: Mqtt Connect Success …
Wed Oct 16 11:13:55 2019 daemon.notice openvpn(sample_client)[1666]: Attempting to establish TCP connection with [AF_INET]OPENVPN_SERVER_IP:1194 [nonblock]
Wed Oct 16 11:13:56 2019 user.notice lora_pkt_fwd[1635]: INFO: [main] concentrator started, packet can now be received
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: TCP connection established with [AF_INET]OPENVPN_SERVER_IP:1194
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: TCPv4_CLIENT link local: [undef]
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: TCPv4_CLIENT link remote: [AF_INET]OPENVPN_SERVER_IP:1194
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: TLS: Initial packet from [AF_INET]OPENVPN_SERVER_IP:1194, sid=02a0b193 73b0691a
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: VERIFY OK: depth=1, CN=ChangeMe
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: Validating certificate key usage
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: ++ Certificate has key usage 00a0, expects 00a0
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: VERIFY KU OK
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: Validating certificate extended key usage
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: VERIFY EKU OK
Wed Oct 16 11:13:56 2019 daemon.notice openvpn(sample_client)[1666]: VERIFY OK: depth=0, CN=server
Wed Oct 16 11:13:57 2019 kern.notice kernel: [ 62.580000] random: nonblocking pool is initialized
Wed Oct 16 11:13:57 2019 user.notice ping-watchdog: wwan wwan0 ifup
Wed Oct 16 11:13:57 2019 user.notice firewall: Reloading firewall due to ifup of wwan (wwan0)
Wed Oct 16 11:13:57 2019 daemon.err openvpn(sample_client)[1666]: Connection reset, restarting [-1]
Wed Oct 16 11:13:57 2019 daemon.notice openvpn(sample_client)[1666]: SIGUSR1[soft,connection-reset] received, process restarting
Wed Oct 16 11:13:57 2019 daemon.notice openvpn(sample_client)[1666]: Restart pause, 5 second(s)
Wed Oct 16 11:13:58 2019 kern.info kernel: [ 64.070000] lora_pkt_fwd uses obsolete (PF_INET,SOCK_PACKET)
Wed Oct 16 11:13:58 2019 daemon.info gwManager[1657]: create_gateway: Create Gateway 60c5a8fffe76121b
Wed Oct 16 11:14:02 2019 daemon.warn openvpn(sample_client)[1666]: WARNING: you are using user/group/chroot/setcon without persist-tun – this may cause restarts to fail
Wed Oct 16 11:14:02 2019 daemon.notice openvpn(sample_client)[1666]: Socket Buffers: R=[87380->87380] S=[16384->16384]
Wed Oct 16 11:14:02 2019 daemon.notice openvpn(sample_client)[1666]: Attempting to establish TCP connection with [AF_INET]OPENVPN_SERVER_IP:1194 [nonblock]
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: TCP connection established with [AF_INET]OPENVPN_SERVER_IP:1194
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: TCPv4_CLIENT link local: [undef]
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: TCPv4_CLIENT link remote: [AF_INET]OPENVPN_SERVER_IP:1194
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: TLS: Initial packet from [AF_INET]OPENVPN_SERVER_IP:1194, sid=9dd37583 9c3c1742
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: VERIFY OK: depth=1, CN=ChangeMe
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: Validating certificate key usage
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: ++ Certificate has key usage 00a0, expects 00a0
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: VERIFY KU OK
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: Validating certificate extended key usage
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: VERIFY EKU OK
Wed Oct 16 11:14:03 2019 daemon.notice openvpn(sample_client)[1666]: VERIFY OK: depth=0, CN=server
Wed Oct 16 11:14:05 2019 daemon.notice openvpn(sample_client)[1666]: Data Channel Encrypt: Cipher ‘AES-256-CBC’ initialized with 256 bit key
Wed Oct 16 11:14:05 2019 daemon.notice openvpn(sample_client)[1666]: Data Channel Encrypt: Using 512 bit message hash ‘SHA512’ for HMAC authentication
Wed Oct 16 11:14:05 2019 daemon.notice openvpn(sample_client)[1666]: Data Channel Decrypt: Cipher ‘AES-256-CBC’ initialized with 256 bit key
Wed Oct 16 11:14:05 2019 daemon.notice openvpn(sample_client)[1666]: Data Channel Decrypt: Using 512 bit message hash ‘SHA512’ for HMAC authentication
Wed Oct 16 11:14:05 2019 daemon.notice openvpn(sample_client)[1666]: Control Channel: TLSv1, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-SHA, 2048 bit RSA
Wed Oct 16 11:14:05 2019 daemon.notice openvpn(sample_client)[1666]: [server] Peer Connection Initiated with [AF_INET]OPENVPN_SERVER_IP:1194
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: SENT CONTROL [server]: ‘PUSH_REQUEST’ (status=1)
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: PUSH: Received control message: ‘PUSH_REPLY,redirect-gateway def1 bypass-dhcp,dhcp-option DNS 172.31.0.2,route-gateway 10.8.0.1,topology subnet,ping 10,ping-restart 120,ifconfig 10.8.0.16 255.255.255.0,peer-id 0’
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: OPTIONS IMPORT: timers and/or timeouts modified
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: OPTIONS IMPORT: --ifconfig/up options modified
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: OPTIONS IMPORT: route options modified
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: OPTIONS IMPORT: route-related options modified
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: OPTIONS IMPORT: peer-id set
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: TUN/TAP device tun0 opened
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: TUN/TAP TX queue length set to 100
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: /sbin/ifconfig tun0 10.8.0.16 netmask 255.255.255.0 mtu 1500 broadcast 10.8.0.255
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: /sbin/route add -net OPENVPN_SERVER_IP netmask 255.255.255.255 gw 10.247.19.204
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: /sbin/route add -net 0.0.0.0 netmask 128.0.0.0 gw 10.8.0.1
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: /sbin/route add -net 128.0.0.0 netmask 128.0.0.0 gw 10.8.0.1
Wed Oct 16 11:14:07 2019 daemon.notice openvpn(sample_client)[1666]: Initialization Sequence Completed
Wed Oct 16 11:14:20 2019 daemon.err mqttEv[1657]: mqttEvDisconnectCB : MqttClient [gwBridgeS Mqtt Client] Disconnected : [7]
Wed Oct 16 11:14:20 2019 daemon.err mqttEv[1657]: mqttEvRdReady: mosquitto [[gwBridgeS Mqtt Client]] loop read ERR: 7
Wed Oct 16 11:14:36 2019 daemon.err mqttEv[1657]: mqttEvReconnect: [gwBridgeS Mqtt Client] Reconnected ERR - [15]
Wed Oct 16 11:14:36 2019 daemon.err mqttEv[1657]: mqttReconnectTimerHandler: Cannot connect …
Wed Oct 16 11:14:51 2019 daemon.err mqttEv[1657]: mqttEvReconnect: [gwBridgeS Mqtt Client] Reconnected ERR - [15]
Wed Oct 16 11:14:51 2019 daemon.err mqttEv[1657]: mqttReconnectTimerHandler: Cannot connect …
Wed Oct 16 11:15:06 2019 daemon.err mqttEv[1657]: mqttEvReconnect: [gwBridgeS Mqtt Client] Reconnected ERR - [15]
Wed Oct 16 11:15:06 2019 daemon.err mqttEv[1657]: mqttReconnectTimerHandler: Cannot connect …
Wed Oct 16 11:15:21 2019 daemon.err mqttEv[1657]: mqttEvReconnect: [gwBridgeS Mqtt Client] Reconnected ERR - [15]
Wed Oct 16 11:15:21 2019 daemon.err mqttEv[1657]: mqttReconnectTimerHandler: Cannot connect …
Wed Oct 16 11:15:25 2019 daemon.info dnsmasq-dhcp[1779]: DHCPREQUEST(br-lan) 192.168.230.113 fc:77:74:d2:3d:ef
Wed Oct 16 11:15:25 2019 daemon.info dnsmasq-dhcp[1779]: DHCPACK(br-lan) 192.168.230.113 fc:77:74:d2:3d:ef DESKTOP-A8RK081
Wed Oct 16 11:15:36 2019 daemon.err mqttEv[1657]: mqttEvReconnect: [gwBridgeS Mqtt Client] Reconnected ERR - [15]
Wed Oct 16 11:15:36 2019 daemon.err mqttEv[1657]: mqttReconnectTimerHandler: Cannot connect …
Wed Oct 16 11:15:48 2019 user.warn lora_pkt_fwd[1635]: [up] Receive Downlink Packet! Drop it
Wed Oct 16 11:15:51 2019 daemon.err mqttEv[1657]: mqttEvReconnect: [gwBridgeS Mqtt Client] Reconnected ERR - [15]
Wed Oct 16 11:15:51 2019 daemon.err mqttEv[1657]: mqttReconnectTimerHandler: Cannot connect …
‘’’
The issue:
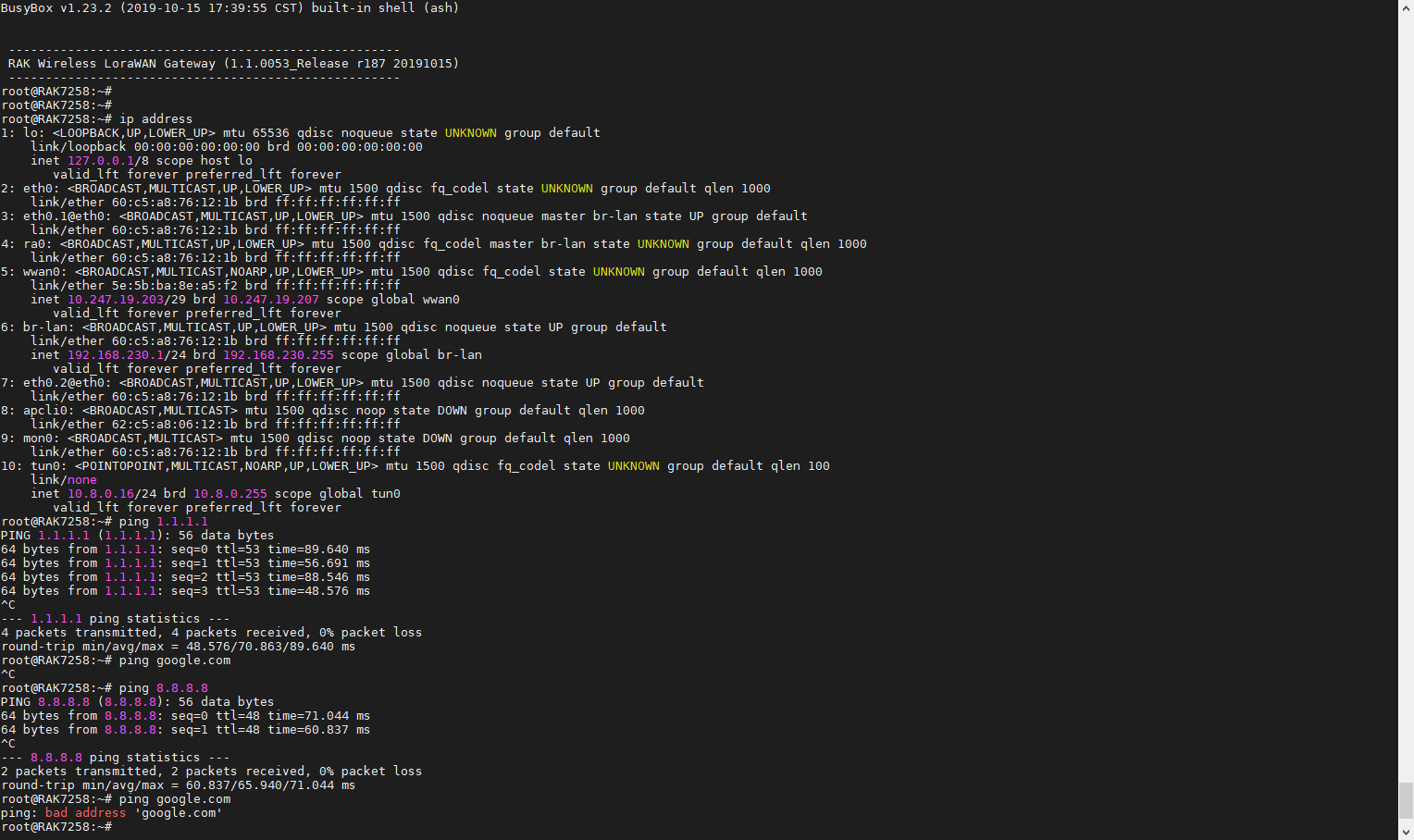
- from the system log above, you can see the OpenVPN is connected
- enter command ip address, you will see it has tun setup with expected static ip address 10.8.0.16
- ping 1.1.1.1 and 8.8.8.8, both are working fine
- however, ping google.com failed, seems the dns is not working
Thanks a lot!
Cheers,
Paul