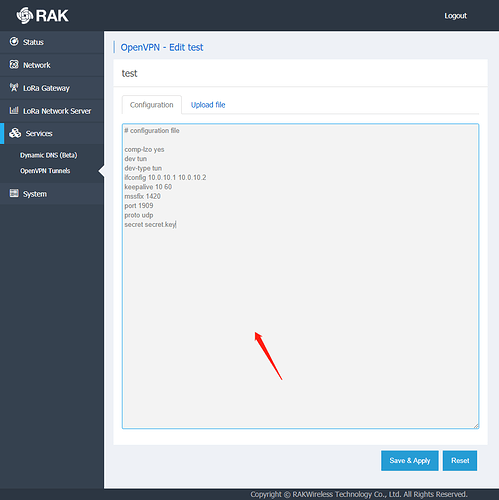
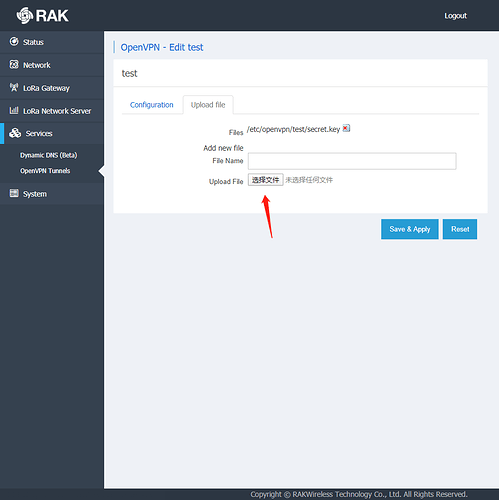
Thanks @yutao
I tried adding the local 192.168.230.1 to the openvpn config file, and commenting out nobind. I however still have the same issue. I performed a factory reset of the gateway yesterday to make sure the settings are all clean.
Server log:
[evening-fields-3890] Tue Mar 17 08:02:49 2020 User connected user_id=5e43a39d852e0f72a703e823
<ethernet unplugged>
[evening-fields-3890] Tue Mar 17 08:04:52 2020 5e43a39d852e0f72a703e823/169.0.122.219 Connection reset, restarting [0]
[evening-fields-3890] Tue Mar 17 08:04:52 2020 User disconnected user_id=5e43a39d852e0f72a703e823
[evening-fields-3890] Tue Mar 17 08:05:44 2020 TCP connection established with [AF_INET6]::ffff:169.0.122.219:1194
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_VER=2.4.3
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_PLAT=linux
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_PROTO=2
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_NCP=2
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_LZO=1
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_COMP_STUB=1
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_COMP_STUBv2=1
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_TCPNL=1
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_HWADDR=60:c5:a8:71:a9:64
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: IV_SSL=OpenSSL_1.0.2j__26_Sep_2016
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: UV_ID=52b5e73dc6c44eb6a5b222c10760f44f
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 peer info: UV_NAME=evening-dreams-8229
[evening-fields-3890] Tue Mar 17 08:05:47 2020 COM> SUCCESS: client-auth command succeeded
[evening-fields-3890] Tue Mar 17 08:05:47 2020 169.0.122.219 [5e43a39d852e0f72a703e823] Peer Connection Initiated with [AF_INET6]::ffff:169.0.122.219:1194
[evening-fields-3890] Tue Mar 17 08:05:47 2020 5e43a39d852e0f72a703e823/169.0.122.219 MULTI_sva: pool returned IPv4=10.0.243.2, IPv6=(Not enabled)
[evening-fields-3890] Tue Mar 17 08:05:48 2020 User connected user_id=5e43a39d852e0f72a703e823
[evening-fields-3890] Tue Mar 17 08:06:34 2020 TCP connection established with [AF_INET6]::ffff:192.143.130.241:1194
[evening-fields-3890] Tue Mar 17 08:07:19 2020 5e43a39d852e0f72a703e823/169.0.122.219 [5e43a39d852e0f72a703e823] Inactivity timeout (--ping-restart), restarting
[evening-fields-3890] Tue Mar 17 08:07:19 2020 User disconnected user_id=5e43a39d852e0f72a703e823
[evening-fields-3890] Tue Mar 17 08:07:34 2020 192.143.130.241 TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)
[evening-fields-3890] Tue Mar 17 08:07:34 2020 192.143.130.241 TLS Error: TLS handshake failed
[evening-fields-3890] Tue Mar 17 08:07:34 2020 192.143.130.241 Fatal TLS error (check_tls_errors_co), restarting
My openvpn config is as follows:
setenv UV_ID <redacted>
setenv UV_NAME <redacted>
client
dev tun
dev-type tun
remote <redacted> 12957 tcp-client
local 192.168.230.1
#nobind
persist-tun
cipher AES-128-CBC
auth SHA1
verb 2
mute 3
push-peer-info
ping 10
ping-restart 60
hand-window 70
server-poll-timeout 4
reneg-sec 2592000
sndbuf 393216
rcvbuf 393216
max-routes 1000
remote-cert-tls server
comp-lzo no
key-direction 1
<ca>
-----BEGIN CERTIFICATE-----
<redacted>
-----END CERTIFICATE-----
</ca>
<tls-auth>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
<redacted>
-----END OpenVPN Static key V1-----
</tls-auth>
<cert>
-----BEGIN CERTIFICATE-----
<redacted>
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
<redacted>
-----END PRIVATE KEY-----
</key>
With ethernet, LTE and the VPN connected my routing table looks like this:
root@RAK7240:~# ip route
default via 192.168.2.1 dev eth0.2 proto static src 192.168.2.10 metric 10
default via 192.143.130.242 dev wwan0 proto static src 192.143.130.241 metric 20
10.0.243.0/24 dev tun0 proto kernel scope link src 10.0.243.3
169.254.0.0/16 dev eth0.2 proto kernel scope link src 169.254.169.100
192.143.130.240/30 dev wwan0 proto static scope link metric 20
192.143.130.242 dev wwan0 proto static scope link src 192.143.130.241 metric 20
192.168.2.0/24 dev eth0.2 proto static scope link metric 10
192.168.2.1 dev eth0.2 proto static scope link src 192.168.2.10 metric 10
192.168.230.0/24 dev br-lan proto kernel scope link src 192.168.230.1
And ip addresses:
root@RAK7240:~# ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether 60:c5:a8:71:a9:64 brd ff:ff:ff:ff:ff:ff
3: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP group default
link/ether 60:c5:a8:71:a9:64 brd ff:ff:ff:ff:ff:ff
4: ra0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel master br-lan state UNKNOWN group default qlen 1000
link/ether 60:c5:a8:71:a9:64 brd ff:ff:ff:ff:ff:ff
5: wwan0: <BROADCAST,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 1000
link/ether d2:63:78:07:c4:93 brd ff:ff:ff:ff:ff:ff
inet 192.143.130.241/30 brd 192.143.130.243 scope global wwan0
valid_lft forever preferred_lft forever
6: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 60:c5:a8:71:a9:64 brd ff:ff:ff:ff:ff:ff
inet 192.168.230.1/24 brd 192.168.230.255 scope global br-lan
valid_lft forever preferred_lft forever
7: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default
link/ether 60:c5:a8:71:a9:64 brd ff:ff:ff:ff:ff:ff
inet 169.254.169.100/16 brd 169.254.255.255 scope global eth0.2
valid_lft forever preferred_lft forever
inet 192.168.2.10/24 brd 192.168.2.255 scope global eth0.2
valid_lft forever preferred_lft forever
8: apcli0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 62:c5:a8:01:a9:64 brd ff:ff:ff:ff:ff:ff
9: mon0: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN group default qlen 1000
link/ether 60:c5:a8:71:a9:64 brd ff:ff:ff:ff:ff:ff
11: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 100
link/none
inet 10.0.243.3/24 brd 10.0.243.255 scope global tun0
valid_lft forever preferred_lft forever
The VPN server’s private IP range is 10.0.243.0/24.