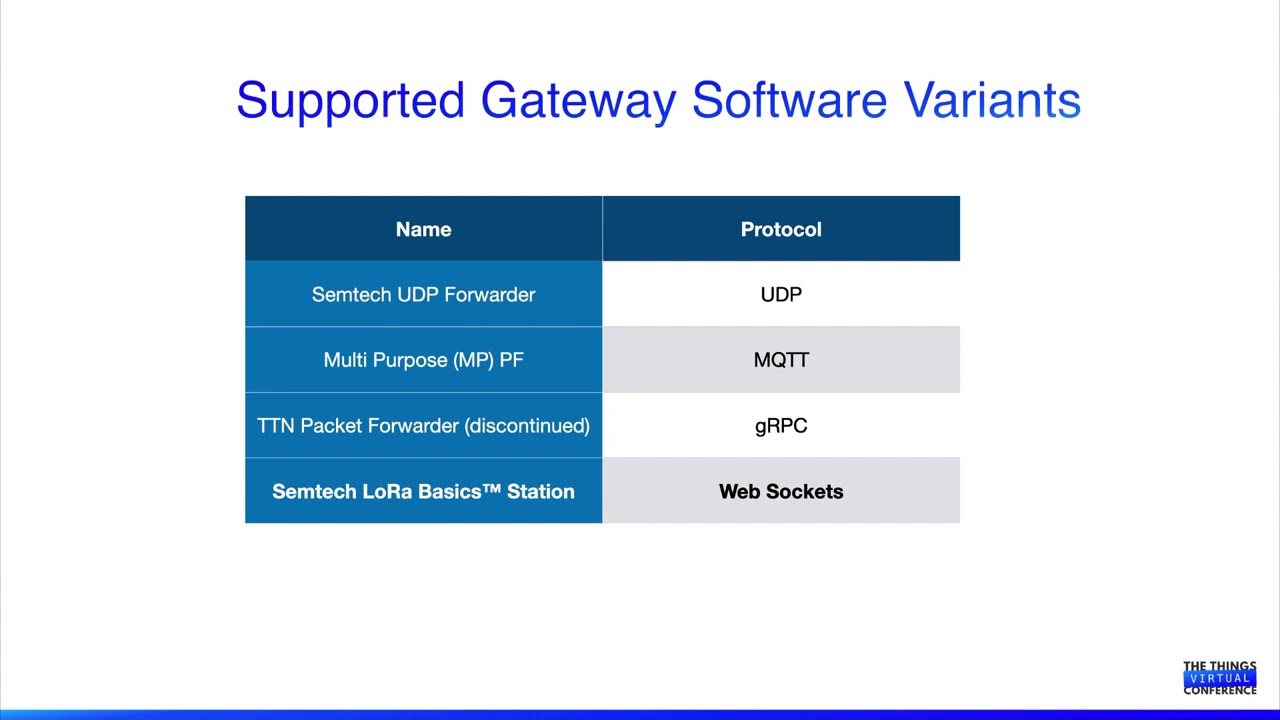
As some of you may know Things Network supports a new packet forwarded protocol called Basic Station.
Basic Station is based on Websockets and introduces extra security and stability compared to the old Semtech UDP protocol. Actually the creators of the original UDP protocol said it was an internal proof of concept which should never have been deployed. So this change is good news!
RAK7240 and RAK7249 firmware from release V1.1.0062_Release_r202 supports Basic Station, but instructions on how to use it have been hard to find. Well wonder no more, here they are in 3 simple steps:
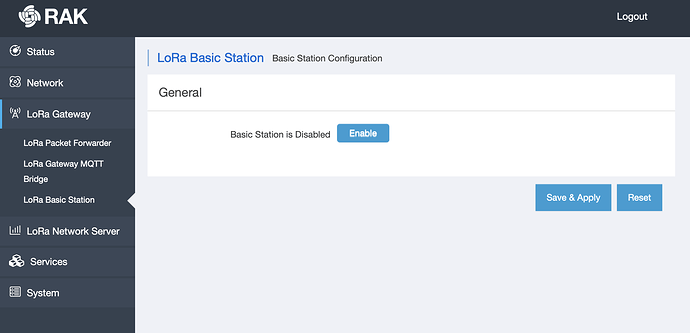
Step 1) Log into the web configuration, go to the new Basic Station tab ard press Enable
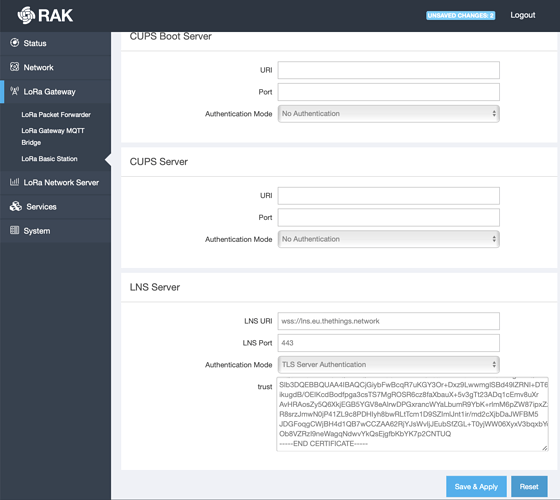
Step 2) Scrolling down go to the LNS server section
For LNS URI enter wss://lns.eu.thethings.network
(“eu” stand for Europe, replace the eu with us, in or au if you’re in the US, India or Australia respectively)
in Authentication mode select “TLS Server Authentication”
and in trust field paste the LetsEncrypt root key in BER format from https://letsencrypt.org/certs/trustid-x3-root.pem.txt
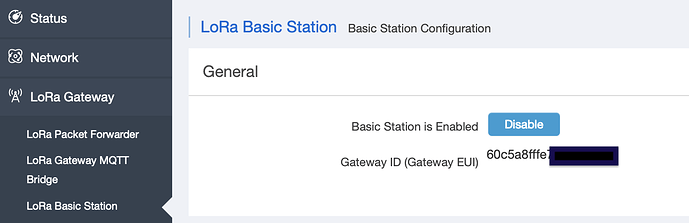
Step 3) Press Save & Apply
Done, you’re gateway will now connect to Things Network using the Basic Station protocol. On the Things Network end everything will be the same as with the Semtech UDP “legacy” protocol, and the gateway should have the same EUI as before.
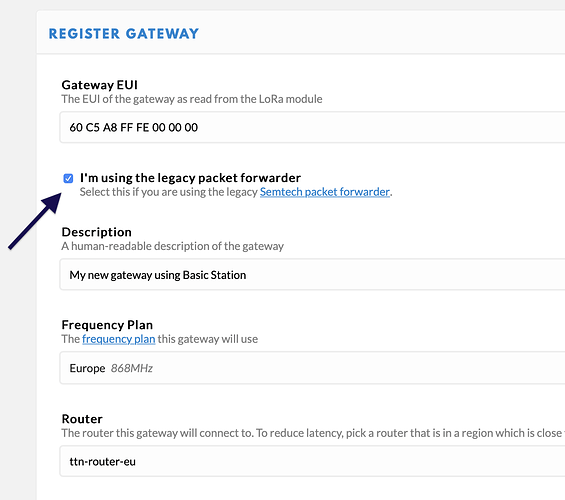
If this is a new gateway you can simply register it on TTN using the EUI shown near the top
and on TTN remember to tick the use legacy packet forwarder box
Hope you found this guide easy but let me know if you have any questions 
Let’s all move to Basic Station protocol as soon as possible and leave the old UDP protocol in the past!